
Sonatype’s Alarming Findings: 156% Surge in Open Source Malware
As the consumption of open source software (OSS) skyrockets, Sonatype’s latest report reveals a staggering 156% increase in open source malware. Since 2019, more than 704,102 malicious packages have been identified, with 512,847 of these unearthed just since November 2023. This alarming discovery is part of Sonatype’s 10th Annual State of the Software Supply Chain report, which underscores a record-breaking year for OSS, estimating around 6.6 trillion downloads in total.
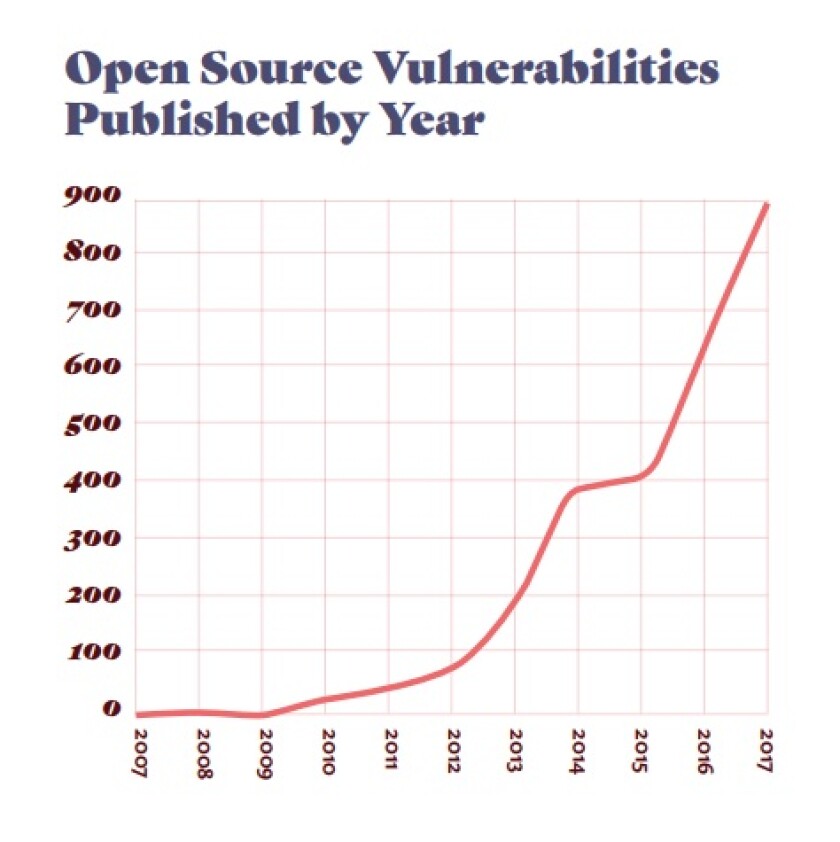 Growth in open source software usage over the years.
Growth in open source software usage over the years.
Of particular note in this report is the dramatic rise in JavaScript (npm) requests, accounting for an astonishing 4.5 trillion requests in 2024 alone—a 70% increase from the previous year. Similarly, the Python Package Index (PyPI), buoyed by the increasing adoption of AI and cloud technologies, is projected to hit 530 billion package requests by the end of this year, marking an 87% year-over-year growth.
Despite the evident progress in OSS usage, organizations face significant hurdles in effective risk management. Sonatype highlights that although the majority of packages offer updated versions (with more than 99% having them available), a staggering 80% of application dependencies have not been upgraded in over a year. It’s especially concerning as 95% of the time when companies use vulnerable components, a fix is already available—a symptom of persistent negligence and complacency in security practices.
The Risks of Vulnerable Open Source Components
The report addresses particular worries around vulnerabilities, illustrating that 13% of Log4j downloads remain susceptible to flaws even three years post the significant Log4shell incident. On top of this, publishers continue to struggle with addressing Common Vulnerabilities and Exposures (CVEs), with some taking more than 500 days to repair. Between 2013 and 2023, there has been a staggering 463% growth in CVEs, emphasizing the urgent need for enhanced vigilance in the OSS realm.
“Over the last decade, we’ve seen software supply chain attacks increase in sophistication and frequency, particularly with the rise of open source malware, while publishers and consumers have remained relatively stagnant when it comes to security,” remarked Brian Fox, CTO and Co-Founder of Sonatype.
Advocating for Stronger Security Practices
As we navigate the complexities posed by open source vulnerabilities, Sonatype urges software manufacturers, consumers, and regulators to embrace robust security measures. The sentiment echoes an essential balance that must be struck between fostering innovation and strengthening security frameworks. Brian Fox further emphasizes the need for proactive security measures, stating, “In order to ensure a vibrant and secure open source ecosystem for the decade ahead, we must build a foundation of proactive security with vigilance against open source malware, decreased consumer complacency, and comprehensive dependency management.”
 Proactive measures in cybersecurity to combat vulnerabilities.
Proactive measures in cybersecurity to combat vulnerabilities.
Global Regulation and Its Impact
Interestingly, the report notes that while challenges persist, regulators are beginning to respond to these trends. Notable new policies are emerging, such as the EU’s updated Network and Information Systems Directive (NIS2), which is set to be enforced starting October 17, 2024, along with forthcoming regulations in countries like India and Australia. These emerging policies are encouraging the adoption of Software Bill of Materials (SBOM), with an impressive 60,000 SBOMs published within the last year.
In sum, the data presented in Sonatype’s research, substantiated by findings from over seven million open source projects, paint a clear picture: as open source continues to proliferate across sectors, the imperative for sophisticated security practices becomes ever more urgent. In doing so, we can hope to cultivate a secure, reliable, and vibrant open source ecosystem that minimizes risks and harnesses innovation to its fullest.
Conclusion
In conclusion, this year serves as a stark reminder of the scale and consequences of ignoring security in the software supply chain. As the stakes increase, so must our commitment to addressing the vulnerabilities that linger within our code. The responsibility falls on all of us—developers, companies, and regulators—to craft a safer digital future that encapsulates the innovative spirit of open source without compromising on security.
 The importance of a secure open source ecosystem for future innovations.
The importance of a secure open source ecosystem for future innovations.














