
Rise of Malware: The Alarming Surge in Open Source Packages
As we witness an unprecedented increase in the consumption of open source software (OSS), recent findings reveal a staggering 156% surge in malicious packages. This alarming trend highlights a growing concern for developers and organizations alike who rely on these resources for their projects.
 Open source projects face increasing security challenges.
Open source projects face increasing security challenges.
Sonatype’s 10th Annual State of the Software Supply Chain report brings this issue to the forefront, revealing that since 2019, over 704,102 malicious packages have been identified, with more than 512,847 of these discovered since November 2023 alone. It’s crucial for us as developers to recognize these threats, particularly as OSS downloads skyrocketed to an estimated 6.6 trillion in 2024. A significant portion of this growth can be attributed to JavaScript (npm) and Python (PyPI), where package requests have reached new heights with an annual growth rate of 70% and 87%, respectively.
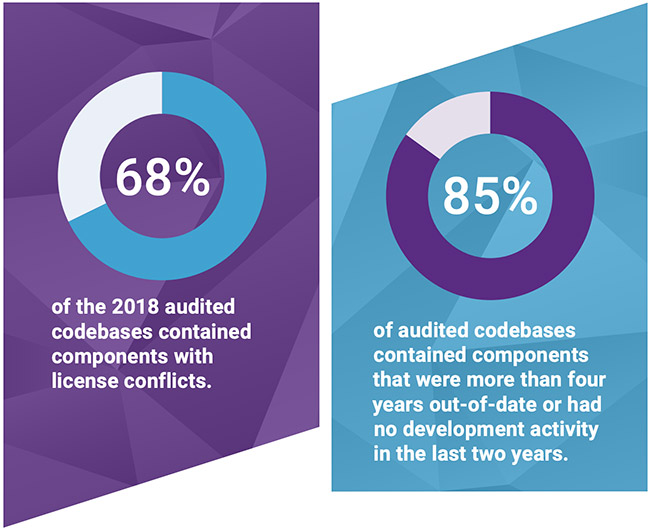
Despite the allure of OSS, we must recognize that every piece of software—whether open source or commercial—has the potential for vulnerabilities. A particularly disconcerting statistic is that 80% of application dependencies remain un-upgraded for over a year, even when more than 99% of packages have updated versions available. This negligence poses significant risks in our software supply chains as we continuously integrate these open source packages into our workflows.
The Persistent Risks of Vulnerable Components
When utilizing vulnerable components, it’s shocking to note that a fixed version already exists 95% of the time. Yet, more than three years after the Log4shell incident, 13% of Log4j downloads remain vulnerable—a stark reminder of the potential impact of ignoring updates. Moreover, software publishers often take over 500 days to remediate vulnerabilities, which is something that must change if we want a secure development environment.
Taking a closer look at the data, from 2013 to 2023, there was a staggering 463% increase in Common Vulnerabilities and Exposures (CVEs). This sharp escalation indicates a lagging response from the community, emphasizing the urgent need for better risk mitigation strategies.
“Over the last decade, we’ve seen software supply chain attacks increase in sophistication and frequency, particularly with the rise of open source malware, while publishers and consumers have remained relatively stagnant when it comes to security,” Brian Fox, CTO and Co-Founder at Sonatype, stated emphatically. This quote resonates deeply with me as a developer who has witnessed the slow progress in addressing these issues.
A Call to Action for Software Manufacturers and Consumers
The responsibility falls on software manufacturers, consumers, and regulators to adopt robust security practices as emphasized in Sonatype’s report. The balance between innovation and security has never been more critical. In my experience, many developers often undervalue the security aspect, focusing instead on rapid development. However, as we’ve seen through these documented trends, the long-term consequences can be dire for organizations that neglect to prioritize security.
 Innovation in software must go hand in hand with security measures.
Innovation in software must go hand in hand with security measures.
Encouragingly, we see regulators starting to grasp the gravity of these security challenges. New policies such as the EU’s updated Network and Information Systems Directive (NIS2), set to become effective on October 17, 2024, alongside anticipated regulations in India and Australia, signify a shift towards a more secure ecosystem for software development.
These regulations bode well for the future of our industry. It’s also exciting to note the adoption of Software Bill of Materials (SBOM), with over 60,000 SBOMs published in the last year alone. Such advancements aim to bolster transparency in software development and could provide a much-needed framework to identify and mitigate risks effectively.
Building a Secure Future in Open Source
In the journey ahead, if we are to secure a vibrant and robust open source ecosystem, we must build a foundation of proactive security measures. This involves cultivating vigilance against open source malware while combating the complacency that has crept into our development processes.
As a community, we need to engage more in discussions about security practices. This includes participating in forums, attending webinars, and staying updated on the latest vulnerabilities affecting our sectors. Personal experiences are invaluable in shaping our responses to these emerging threats.
To conclude, as developers, we must collectively embrace the call for action from firms like Sonatype. It’s not merely about integrating the latest tools and technologies into our arsenal but ensuring we do so while adhering to a strong security posture. Only through consistent effort and awareness can we hope to navigate the challenges posed by an expanding landscape of open source software threats. Let’s work together to protect our innovations and usher in a safer future.
 The importance of security in open source development cannot be overstated.
The importance of security in open source development cannot be overstated.















